CCNPv8 ENCOR (Version 8.0) – Multicast and QoS Exam
- 224.0.1.49
- 224.0.0.1
- 224.0.0.40
- 224.0.1.39
2. Which is a characteristic of PIM sparse mode?
- It uses a pruning mechanism to stop the flow of unwanted multicast traffic on interfaces with no downstream neighbors.
- It requires an RP on the network to act as the root of the shared distribution tree.
- It builds the multicast tree by flooding traffic out all interfaces.
- It is designed for networks where receivers are located on every subnet in the network.
3. The bootstrap router (BSR) mechanism of automating the distribution of rendezvous point (RP) information uses which IP address to disseminate information to all protocol independent multicast (PIM) routers?
- 224.1.0.13
- 224.0.0.13
- 224.1.1.13
- 224.0.1.13
4. A network administrator is troubleshooting an IP multicast problem. Where can the administrator view source S, group G, incoming interfaces (IIF), outgoing interfaces (OIFs), and RPF neighbor information for each multicast route?
- in unicast routing table
- in the routing information base
- in the multicast forwarding information base
- in the multicast routing information base
5. A network administrator statically assigns a multicast address of 239.255.8.5 to an application running on a server. The NIC on the server is with the MAC address of AB.54.C1.01.B8.9F. Which Layer 2 multicast address will receivers use on their interfaces in order to receive the multicast feed?
- 01:00:5E:01:B8:9F
- AB:54:C1:17:A8:02
- 01:00:5E:7F:08:05
- AB:54:C1:7F:08:05
6. Which notation is used to refer to the forwarding state in PIM shared trees?
- (*,G)
- (S,G)
- (*,S)
- (G,S)
7. Which statement about IGMPv3 is true?
- It sends IGMP query messages with a TTL value of 1 addressed to the all-host group (224.0.0.1).
- It rejects any group-specific query message that is sent from the hosts that want to join a multicast group.
- It enables a multicast receiver to signal to the first hop router the multicast sources from which it expects to receive traffic.
- It does not accept a leave group message from the hosts that have already joined the multicast group.
8. Which well-know multicast group is joined by all PIM-enabled routers to receive RP mappings?
- 224.0.0.2
- 224.0.0.13
- 224.0.1.40
- 224.0.1.39
9. An administrator has configured and enabled multicast together with PIM sparse mode on all VLANs on the network. Which feature helps to reduce multicast traffic being broadcast on the access layer switches?
- source registration
- PIM Pruning
- IGMP snooping
- SPT switchover
10. Which two IGMPv3 modes are used to signal membership to a multicast host group? (Choose two.)
- preclude
- join
- include
- rendezvous
- exclude
- leave
11. Which statement describes a characteristic of IP multicast routing?
- PIM hello messages are sent every 60 seconds by default out each PIM enabled interface.
- PIM dense mode flood and prune behavior repeats every three minutes.
- PIM sparse mode builds the multicast tree through flooding of traffic out every interface.
- PIM sparse mode and PIM dense mode require an RP on the network.
12. To which multicast group does a candidate RP send announcement messages to advertise its willingness to be an RP?
- 224.0.0.13
- 224.0.1.40
- 224.0.1.39
- 224.0.0.2
13. Which two statements about Protocol Independent Multicast (PIM) are true? (Choose two.)
- Three of the forwarding modes for PIM are PIM dense mode (PIM-DM), PIM sparse mode (PIM-SM), and PIM sparse-dense mode.
- PIM is a multicast routing protocol that makes packet-forwarding decisions independent of the unicast IP routing protocol that is running in the network.
- PIM should be configured on the device that hosts the source of the muticast traffic.
- PIM sparse mode is most useful when there are few senders, many receivers, and the volume of multicast traffic is high.
- PIM should be configured only on the first and the last hop routers in the multicast tree.
- PIM does not require an IGP protocol to be configured in the network.
14. Which two statements describe IGMP? (Choose two.)
- IGMPv2 supports multicast source filtering.
- IGMPv1 only supports queries sent to a predefined group.
- IGMPv3 provides support for SSM.
- An IGMPv2 router will only allow IGMPv2 hosts to execute a join request.
- Multicast flooding on a LAN segment can be mitigated by using IGMP snooping.
15. Which nonproprietary mechanism does PIM use to discover and announce RP set information for each group prefix for all the routers in a PIM domain?
- Static RP
- BSR
- RPF
- Auto-RP
16. What happens when an edge router using IntServ QoS determines that the data pathway cannot support the level of QoS requested?
- Data is forwarded along the pathway using IntServ but not provided preferential treatment.
- Data is forwarded along the pathway using DiffServ.
- Data is forwarded along the pathway using a best-effort approach.
- Data is not forwarded along the pathway.
17. Question as presented: Match the state with its marking in a DSCP two token bucket mechanism environment. (Not all options apply.)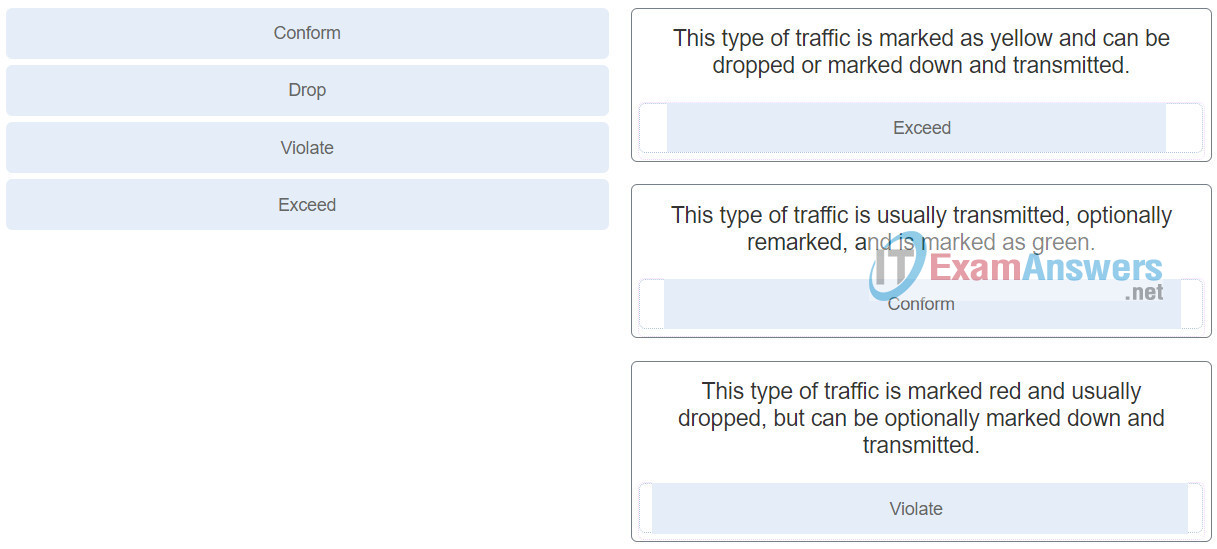
18. What two fields are available in IPv4 and IPv6 headers to mark packets for QoS? (Choose two.)
- Traffic Class
- Class of Service
- Type of Service
- Priority
- VLAN ID
19. A network administrator has defined the trust boundary of a network. What is the function of trusted endpoints deployed across the network?
- Trusted endpoints are devices designed to provide network security features.
- Trusted endpoints provide monitoring and logging solutions.
- Trusted endpoints have the ability to mark application traffic.
- Trusted endpoints provide the ability to drop previously marked traffic during congestions.
20. Which is a QoS model that a network engineer would implement to ensure a source to destination quality of service standard for a specified data flow?
- best effort
- low latency queuing
- differentiated services
- class-based weighted fair queuing
- integrated services
21. What would be the Tc value in ms for a 1 Gbps interface configured with a policer defined with a CIR of 150 Mbps and a Bc of 12 Mb?
- 10,000 ms
- 1000 ms
- 100 ms
- 10 ms
22. What statement describes the Class of Service field?
- It is a Layer 2 field.
- It is a field that is 6 bits long.
- It is a field that is 8 bits long.
- It is a Layer 1 field.
23. Which protocol operates at Layer 3 and is used for marking packets?
- CoS
- IntServ
- DSCP
- QoE
24. What is the recommended maximum one-way latency when implementing video over IP for real-time video applications?
- Latency is not a factor for smooth video over IP implementation.
- Latency should be defined for voice traffic only (not for video).
- The recommended maximum one-way latency should not be more than 150 ms.
- When mixed video and voice packets are included in the video stream, the latency should be 300 ms.
25. Which two procedures should be implemented when deploying VoIP in a campus network? (Choose two.)
- voice and data traffic in the same VLAN and mark the traffic for high priority treatment
- a traffic shaping QoS policy to guarantee minimum delay for the voice traffic
- packet marking for voice traffic with a 802.1p CoS value of 5
- priority queuing with voice traffic given the high-priority queue
- a voice class low-latency queuing (LLQ) QoS policy
26. Which statement is true about the Single-Rate Two-Color Markers algorithm?
- It uses a two bucket algorithm and traffic can be classified as conforming to, exceeding, or violating the CIR.
- It uses a single token bucket algorithm and traffic can be marked or dropped in both states (conforming to or exceeding the CIR).
- It uses a two bucket algorithm that causes fewer TCP transmissions and is more efficient for bandwidth utilization.
- It uses a single bucket algorithm and uses three colors or states to classify the traffic.
27. Question as presented: Match the queuing algorithm with its description. (Not all options apply.)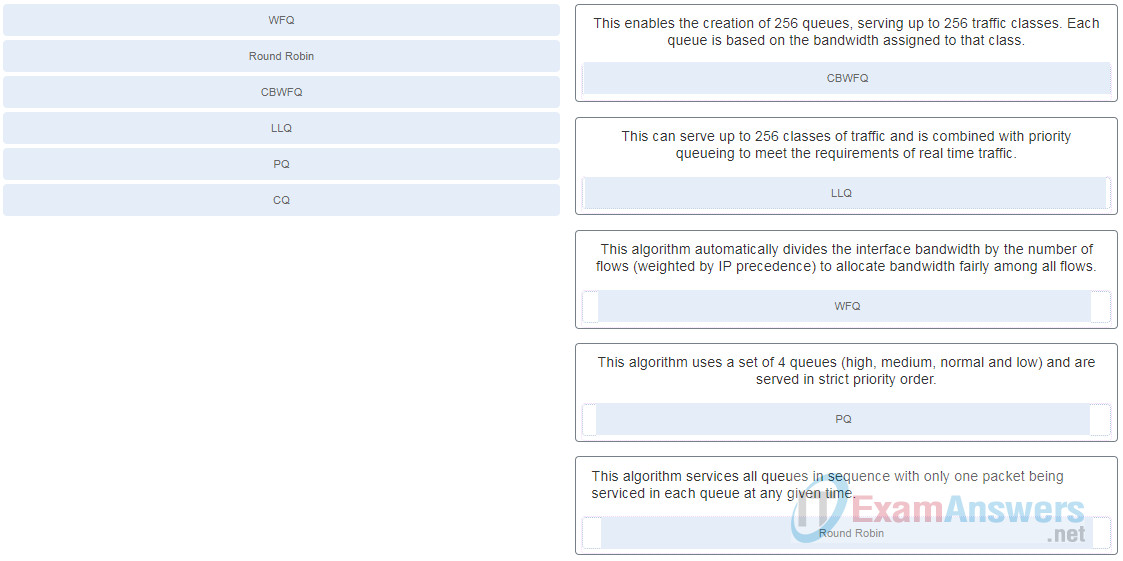
28. What is the value of the DSCP marker for video traffic on a WLAN?
- AF41
- O
- AF11
- EF
29. Which statement describes NBAR2?
- NBAR2 can identify a variety of protocols and applications by using up to Layer 6 data.
- NBAR2 supports only scavenger traffic.
- NBAR2 uses MQC to match traffic to specific protocols.
- NBAR2 does not require monthly protocol packs to identify new and emerging applications.
30. Match QoS techniques with the description. (Not all options are used.)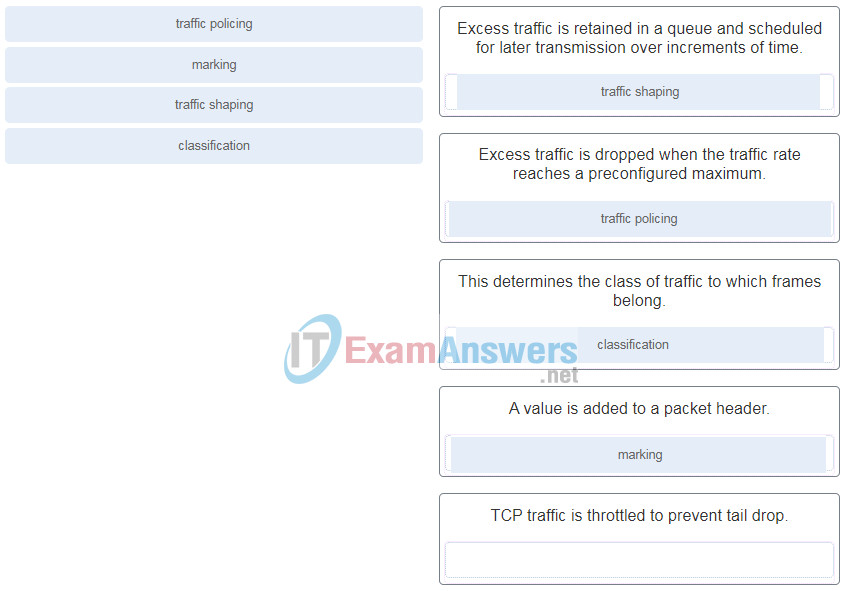
31. Match the parameter with the correct description. (Not all options apply.)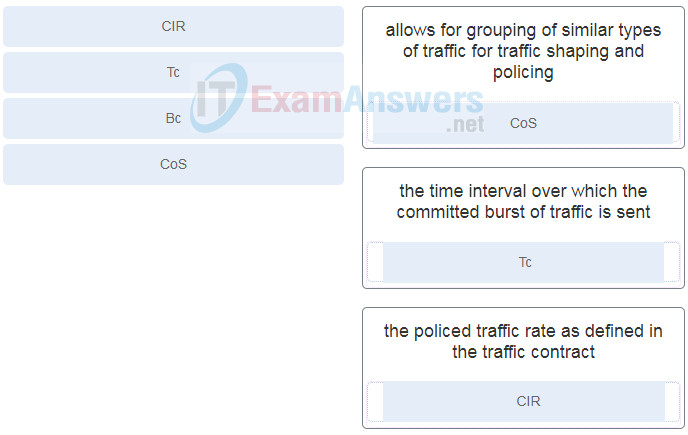
32. Match the operation to the appropriate QoS model.







