CCNPv8 ENCOR (Version 8.0) – Virtualization, Automation, and Programmability Exam
1. Which term defines a software emulation of a physical server with an operating system?
- Guest OS
- container image
- container
- virtual machine
2. What component enables VMs within a virtualized server environment to communicate with each other and with external networks?
- guest OS
- container engine
- vSwitch
- hypervisor
3. What are three responsibilities of the the NFV virtualized infrastructure manager? (Choose three.)
- performing all FCAPS functions for VNFs
- managing and controlling NFVI hardware resources
- performing life cycle management of all NFVI resources
- creating, maintaining, and tearing down VNF network services
- creating an end-to-end network
- collecting performance measurements and fault information
4. Which two components of the ETSI NFV architectural framework make up the NFV management and orchestration (MANO)? (Choose two.)
- Virtualized Infrastructure Manager
- NFV infrastructure
- NFV element manager
- OSS/BSS
- NFV orchestrator
5. In an Open vSwitch (OVS) architecture, which component resides in the kernel space and forwards packets from the network stack to the vNIC of the VM?
- emulated PCIe device
- vSwitch
- pNIC driver
- pNIC
6. What term is used to define the software process that creates VMs and performs hardware abstraction to support VMs?
- hypervisor
- Virtualized Infrastructure Manager (VIM)
- container
- element manager
7. What function does Cisco DNA Center provide as part of a Cisco enterprise NFV solution?
- VNF life cycle management, monitoring, device programmability, and hardware acceleration
- communication between different VNFs and to the outside world
- CPU, memory, and storage resources to run NVFs and applications
- VNF management and orchestration
8. Question as presented: Match each VNF term to its description.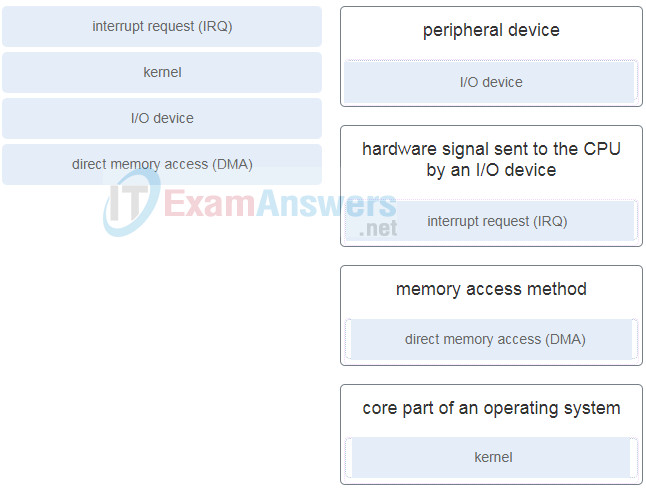
- peripheral device
- hardware signal sent to the CPU by an I/O device
- memory access method
- core part of an operating system
9. What is a limitation when PCI Passthrough is deployed?
- CPU utilization in increased.
- VNFs cannot share pNICs.
- Traffic between VNFs must be switched by an external switch.
- A dedicated CPU core is required to poll pNICs and process incoming data.
10. What is the function provided by the OSS/BSS components of the ETSI NFV architectural framework?
- They collect performance measurements and fault information.
- They support network systems and services that run business operations.
- They perform all FCAPS functions for VNFs.
- They perform life cycle management of all NFVI resources.
11. Which two HTTP functions correspond to the UPDATE function in CRUD? (Choose two.)
- PUT
- DELETE
- PATCH
- GET
- POST
12. What are two syntax rules for writing a JSON array? (Choose two.)
- A semicolon separates the key and list of values.
- A space must separate each value in the array.
- The array can include only one value type.
- Values are enclosed in square brackets.
- Each value in the array is separated by a comma.
13. Refer to the exhibit. Which data format is used to represent the data for network automation applications?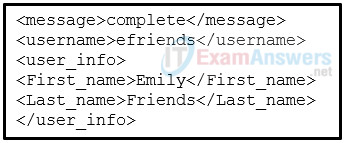
- YAML
- XML
- JSON
- HTML
14. Which API does the Cisco DNA Center controller use for user authentication?
- Fabric Device
- Network Device
- Authentication
- Token
15. Refer to the exhibit. What is the meaning of the config false statement under the observed-speed leaf node?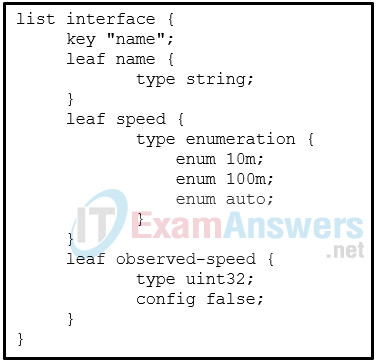
- The value of the leaf node is a comment string.
- The value of the leaf node is the default value.
- The value of the leaf node cannot be configured.
- The value of the leaf node has not been configured yet.
16. Which statement describes the function of GitHub?
- It is an online game site.
- It is a service provider for virtualized servers and applications.
- It is a hosted web-based repository for code.
- It is an online storage service for personal files.
17. Which type of API is used to carry configuration changes from a network controller to individual network devices in network automation applications?
- lower layer
- southbound
- eastbound
- northbound
18. Refer to the exhibit. Which data format is used to represent the data for network automation applications?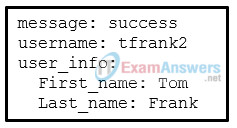
- YAML
- JSON
- HTML
- XML
19. A network administrator is checking and making configuration changes on a network device from home. What are two ways to secure the connection between the command-line interface (CLI) of the network device and the remote workstation used by the administrator? (Choose two.)
- through a Telnet connection
- through an SSH connection
- through a virtual terminal application
- through an HTTP interface
- through a VPN connection
20. What is the characteristic of the Postman application that relates to using APIs?
- It provides a GUI to interact with remote workstations.
- It is a web-based application to connect to various network devices.
- It is a web-based email client.
- It uses a console-based approach to interact with APIs.
21. The following program was created in Python.
user_input = int( input(" What is 3 * 2? "))
if (user_input = 6):
print (" Correct!")
else: print (" Incorrect...")Why does the program result in an error?
- There should be double equal signs when checking conditional equality.
- The quotation mark is not needed in the print function.
- 3 * 2 does not equal 6.
- The user_input variable was not defined.
22. In a hosted Chef type of deployment, where is the Chef server located?
- on a LAN located near to the other chef components
- in the cloud
- on a workstation
- in the enterprise core
23. Which term is used to describe a set of instructions for execution by the configuration management tool Puppet?
- Manifest
- Playbook
- Cookbook
- Pillar
24. Question as presented: Match the automation tool with the description.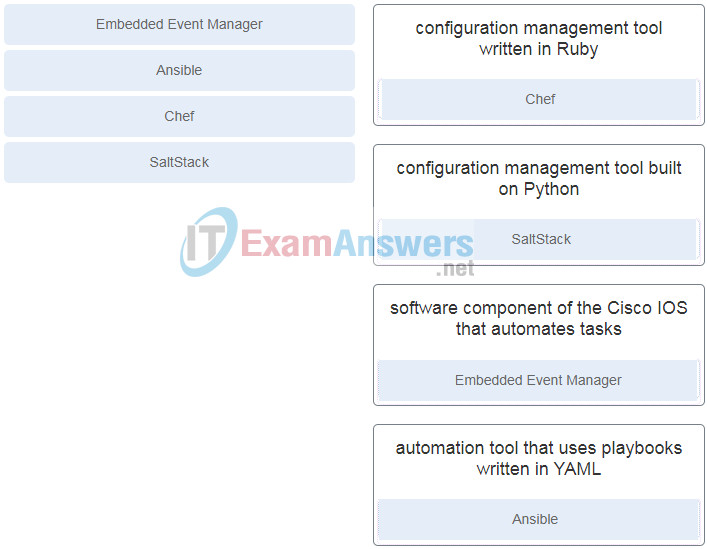
- configuration management tool written in Ruby
- configuration management tool built on Python
- software component of the Cisco IOS that automates tasks
- automation tool that uses playbooks written in YAML
25. What is the SaltStack agent called that runs on nodes?
- station
- reactor
- minion
- chef
26. A student is studying in preparation for an interview for a job in programming and network automation. What is a characteristic of Ansible ?
- It is an agentless automation tool.
- It is a programming interface that communicates from a network controller to its management software.
- It is a hosted web-based repository that uses version control for storing and sharing code.
- It is a free online tool that can check the format of programmed files to verify that they have valid syntax.
27. Which statement describes the Cisco Embedded Event Manager?
- It is a security policy management platform that provides highly secure network access control (NAC) to users and devices.
- It is a centralized management platform that aggregates and correlates threat events.
- It is a collector and aggregator of network telemetry data that performs network security analysis and monitoring.
- It is a Cisco IOS tool that allows engineers to build task automation software applets.
28. Which configuration management tool uses an agentless approach?
- Ansible
- Chef
- SaltStack
- Puppet
29. Question as presented: Match the Ansible Playbook structure component to the use case.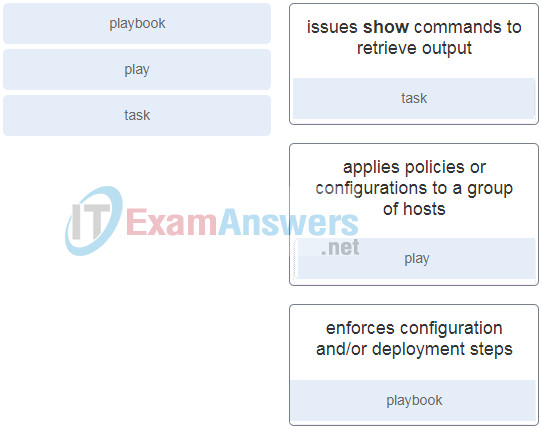
- issues show commands to retrieve output
- applies policies or configurations to a group of hosts
- enforces configuration and/or deployment steps
30. In which type of deployment is the Chef server hosted in the cloud?
- private Chef
- hosted Chef
- Chef Solo
- Chef Client and Server
31. What is a characteristic of the Cisco Embedded Event Manager?
- It uses playbooks written in YAML to deploy configuration changes.
- It is a software component of the Cisco IOS.
- It is built on Python and has a Python programming interface.
- It is an open source tool based on the Ruby language.
32. Which language is used to write Ansible playbooks?
- YANG
- YAML
- Python
- JSON
33. A student is studying in preparation for an interview for a job in programming and network automation. What is a characteristic of Chef?
- It is a free online tool that can check the format of programmed files to verify that they have valid syntax.
- It is a hosted web-based repository that uses version control for storing and sharing code.
- It is an open source configuration management tool that is designed to automate configurations and operations of a network and server environment.
- It is a markup programming language.
34. A student is studying in preparation for an interview for a job in programming and network automation. What is a characteristic of GitHub ?
- It is an application that can interact with APIs using a console-based approach and allows various data types and formats to interact with REST-based APIs.
- It is a hosted web-based repository that uses version control for storing and sharing code.
- It is an acronym that describes functions that most applications or databases use to store or alter data.
- It is a data format that stores all of its information in key/value pairs and surrounds each object with curly braces.
35. A student is studying in preparation for an interview for a job in programming and network automation. What is a characteristic of CRUD ?
- It is a data model that describes what can be configured, monitored, executed, and reset on a device.
- It is a markup programming language.
- It is a free online tool that can check the format of programmed files to verify that they have valid syntax.
- It is an acronym that describes functions that most applications or databases use to store or alter data.
36. What is a characteristic of a virtual machine?
- It is lightweight and small in size.
- It leverages the kernel of the host OS for fast load times.
- It is equipped with a guest OS.
- It includes only components required to run an application.
37. What is JSON?
- It is a database.
- It is a compiled programming language.
- It is a data format for storing and transporting data.
- It is a scripting language.
38. A student is studying in preparation for an interview for a job in programming and network automation. What is a characteristic of SaltStack SSH ?
- It is a programming interface that takes changes made to the management software and pushes the changes down to the individual devices.
- It is an acronym that describes functions that most applications or databases use to store or alter data.
- It is a programming interface that communicates from a network controller to its management software.
- It is an agentless option of a configuration management tool that allows users to run commands without having to install an agent on the remote device or node.
39. A student is studying in preparation for an interview for a job in programming and network automation. What is a characteristic of Puppet ?
- It is a free online tool that can check the format of programmed files to verify that they have valid syntax.
- It is a configuration management and automation tool with a downloadable Cisco module to support Cisco devices.
- It is a hosted web-based repository that uses version control for storing and sharing code.
- It is a markup programming language.







